Hilfe mit VPN - Zertifikate Mikrotik - Shrew VPN
Hallo,
Ich bin in Deutschland seit 4 monat, deshalb bin ich noch nicht mit Deutsch gut. Ich hoffe, dass es ok ist, dass ich in englisch sprechen.
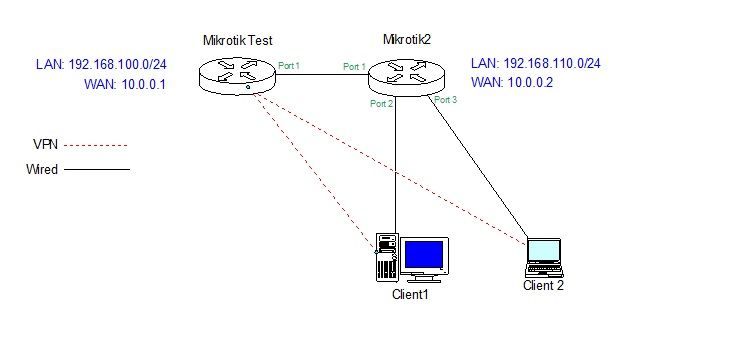
I'm trying to do the next scenario for testing purposes (all inside LAN, without going out internet) using Mikrotik and Shrew VPN:
After a long fight I was able to connect using RSA Signatures, I created the certificates in mikrotik as follow here: http://wiki.mikrotik.com/wiki/Manual:Create_Certificates
But when I revoke the client1 or client2 certificate and kill the connection I'm still able to connect.
Most likely I'm doing something wrong, but I don't know what to try anymore...
I add here the configuration of shrew and mikro for if someone have an idea
Mikrotiktest
In mikrotik2 I've only configured LAN WAN and ip routes.
Any tip or help would be very apreciated
Mit freundlichen Grüßen
Nova
Ich bin in Deutschland seit 4 monat, deshalb bin ich noch nicht mit Deutsch gut. Ich hoffe, dass es ok ist, dass ich in englisch sprechen.
I'm trying to do the next scenario for testing purposes (all inside LAN, without going out internet) using Mikrotik and Shrew VPN:
After a long fight I was able to connect using RSA Signatures, I created the certificates in mikrotik as follow here: http://wiki.mikrotik.com/wiki/Manual:Create_Certificates
But when I revoke the client1 or client2 certificate and kill the connection I'm still able to connect.
Most likely I'm doing something wrong, but I don't know what to try anymore...
I add here the configuration of shrew and mikro for if someone have an idea
n:version:4
n:network-ike-port:500
n:network-mtu-size:1380
n:client-addr-auto:1
n:network-natt-port:4500
n:network-natt-rate:15
n:network-frag-size:540
n:network-dpd-enable:0
n:client-banner-enable:0
n:network-notify-enable:0
n:client-dns-used:1
n:client-dns-auto:1
n:client-dns-suffix-auto:1
n:client-splitdns-used:1
n:client-splitdns-auto:1
n:client-wins-used:1
n:client-wins-auto:1
n:phase1-dhgroup:2
n:phase1-keylen:256
n:phase1-life-secs:86400
n:phase1-life-kbytes:0
n:vendor-chkpt-enable:0
n:phase2-keylen:256
n:phase2-life-secs:28800
n:phase2-life-kbytes:0
n:policy-nailed:1
n:policy-list-auto:0
b:auth-server-cert-xxxx
b:auth-client-cert-xxxxx
b:auth-client-key- xxxxx
s:auth-client-cert-name:cert_export_client1.crt
s:auth-client-key-name:cert_export_client1.key
s:auth-server-cert-name:cert_export_ca.crt
s:network-host:10.0.0.1
s:client-auto-mode:pull
s:client-iface:virtual
s:network-natt-mode:enable
s:network-frag-mode:enable
s:auth-method:mutual-rsa
s:ident-client-type:asn1dn
s:ident-server-type:asn1dn
s:phase1-exchange:main
s:phase1-cipher:aes
s:phase1-hash:sha1
s:phase2-transform:esp-aes
s:phase2-hmac:sha1
s:ipcomp-transform:disabled
n:phase2-pfsgroup:2
s:policy-level:require
s:policy-list-include:10.0.0.1 / 255.255.255.255Mikrotiktest
/ip address
add address=192.168.100.1/24 comment=LAN disabled=no interface=ether2 \
network=192.168.100.0
add address=10.0.0.1/24 comment=WAN disabled=no interface=ether1 network=\
10.0.0.0
/ip route
add !bgp-as-path !bgp-atomic-aggregate !bgp-communities !bgp-local-pref \
!bgp-med !bgp-origin !bgp-prepend !check-gateway disabled=no distance=1 \
dst-address=0.0.0.0/0 gateway=ether1 !route-tag !routing-mark scope=30 \
target-scope=10
add !bgp-as-path !bgp-atomic-aggregate !bgp-communities !bgp-local-pref \
!bgp-med !bgp-origin !bgp-prepend !check-gateway disabled=no distance=1 \
dst-address=192.168.110.0/24 gateway=10.0.0.2 !route-tag !routing-mark \
scope=30 target-scope=10
/ip ipsec mode-config
set (unknown) name=request-only send-dns=yes
/ip ipsec policy group
set default name=default
add name=RoadWarriors
/ip ipsec proposal
set [ find default=yes ] auth-algorithms=sha1 disabled=no enc-algorithms=\
aes-256-cbc lifetime=8h name=default pfs-group=modp1024
/ip pool
add name=dhcp_pool1 ranges=192.168.100.10-192.168.100.50
add name=ipsec ranges=192.168.130.51-192.168.130.150
/ip dhcp-server
add address-pool=dhcp_pool1 authoritative=after-2sec-delay bootp-support=\
static disabled=no interface=ether2 lease-script="" lease-time=3d name=\
dhcp1
/ip ipsec mode-config
add address-pool=ipsec address-prefix-length=24 name=cfg1 send-dns=yes \
split-include=0.0.0.0/0
/ip ipsec peer
add address=0.0.0.0/0 auth-method=rsa-signature certificate=server dh-group=\
modp1024 disabled=no dpd-interval=disable-dpd dpd-maximum-failures=5 \
enc-algorithm=aes-256 exchange-mode=main generate-policy=port-overrade \
hash-algorithm=sha1 lifebytes=0 lifetime=1d local-address=0.0.0.0 \
mode-config=cfg1 nat-traversal=yes passive=yes policy-template-group=\
RoadWarriors port=500 proposal-check=obey remote-certificate=none \
send-initial-contact=no
/ip ipsec policy
set 0 disabled=no dst-address=0.0.0.0/32 group=default proposal=default \
protocol=all src-address=0.0.0.0/32 template=yes
add disabled=no dst-address=0.0.0.0/0 group=RoadWarriors proposal=default \
protocol=all src-address=192.168.130.0/24 template=yesIn mikrotik2 I've only configured LAN WAN and ip routes.
Any tip or help would be very apreciated
Mit freundlichen Grüßen
Nova
Please also mark the comments that contributed to the solution of the article
Content-Key: 255506
Url: https://administrator.de/contentid/255506
Printed on: April 25, 2024 at 15:04 o'clock
2 Comments
Latest comment
For being just 4 month in Germany your German sounds excellent. No problem with English....
In your MT config there is the /certificate section missing. Is that done intentionally due to security reasons ?
Which option did you use following the MT instruction ? Generating them on the MT itself or did you use the OpenSSL option ?
A lot of questions but this was not quite clear in your description.
P.S.: Dont be so formal with "Mit freundlichen Grüßen" In forums like these we follow the golden German rule You can say "you" to me
In forums like these we follow the golden German rule You can say "you" to me 
In your MT config there is the /certificate section missing. Is that done intentionally due to security reasons ?
Which option did you use following the MT instruction ? Generating them on the MT itself or did you use the OpenSSL option ?
A lot of questions but this was not quite clear in your description.
P.S.: Dont be so formal with "Mit freundlichen Grüßen"