VPN IPSec mit Linksys Router funktioniert nicht
Hallo Liebes Forum,
ich habe ein Netzwerk mit einem Linksys WRV200 Router. Der Router hat die aktuelle Firmware Version. Provider ist Unitymedia mit öffentlicher dynamischer IPv4 IP.
Einziges Gerät im Netz ist ein Macbook (über WLAN).
Internet funktioniert einwandfrei, aber den VPN-IPSec-Servers vom Router bekomme ich nicht ans Laufen.
Folgende Einstellungen habe ich am Router vorgenommen:
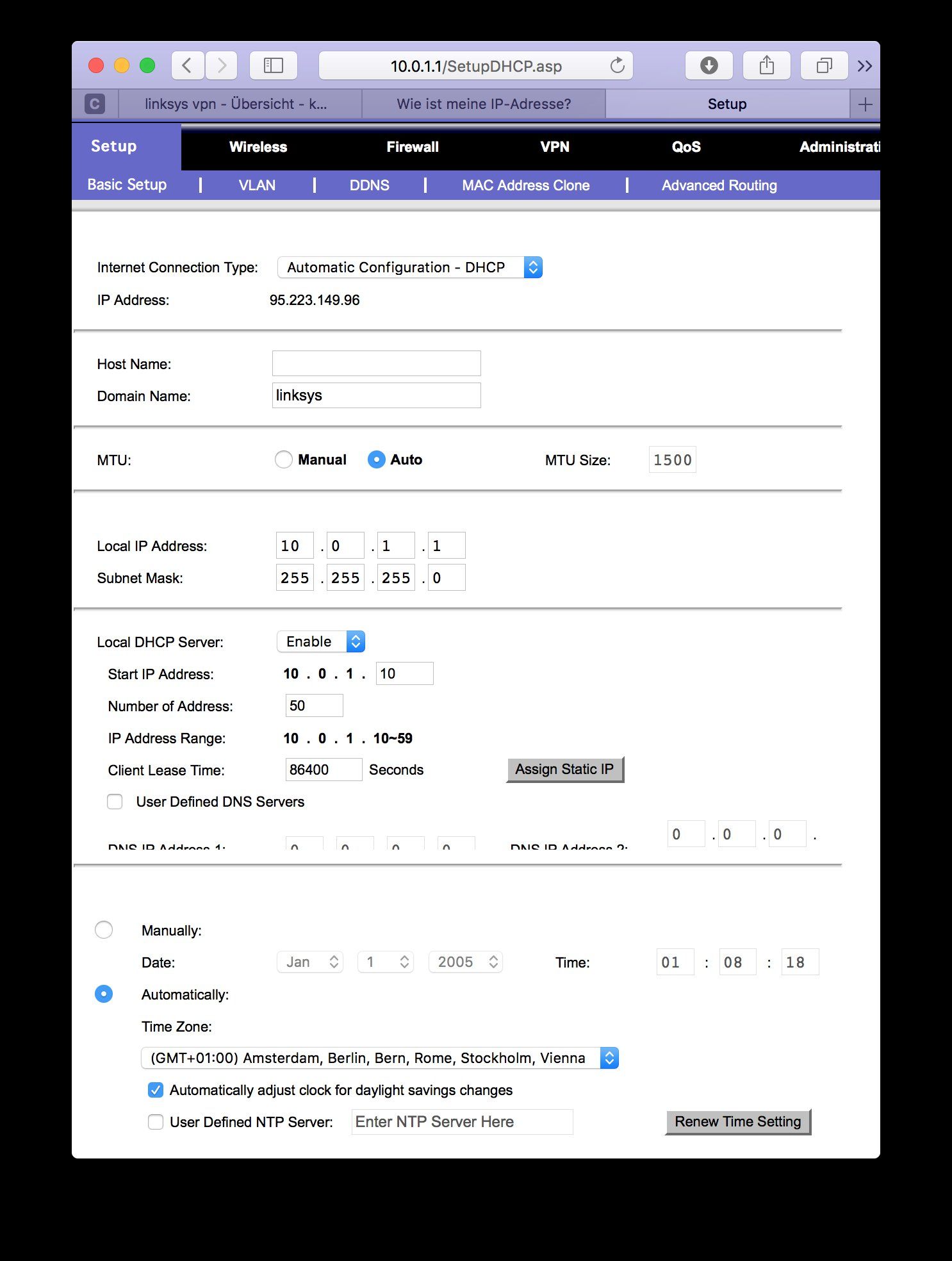
WAN und DHCP:
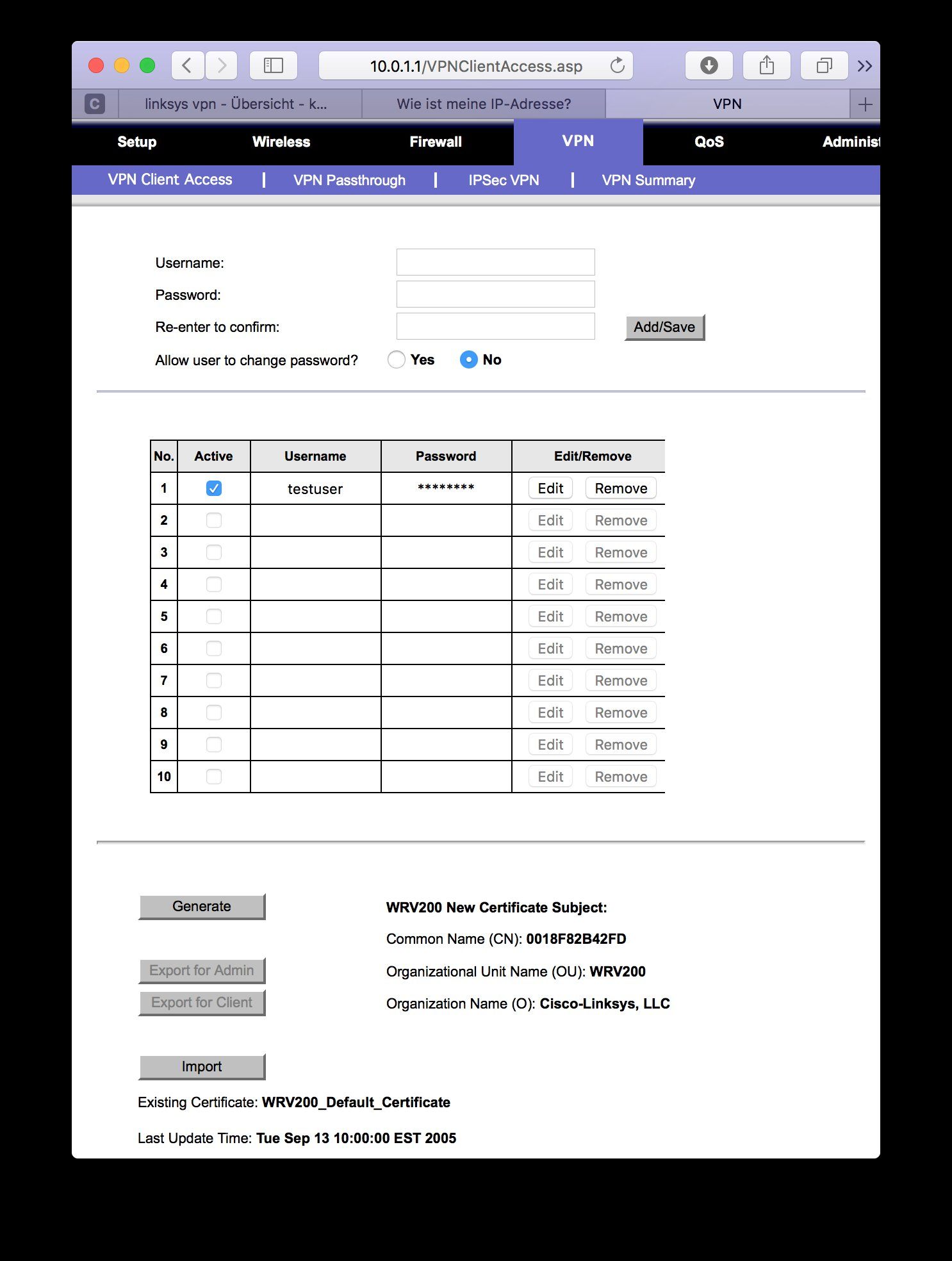
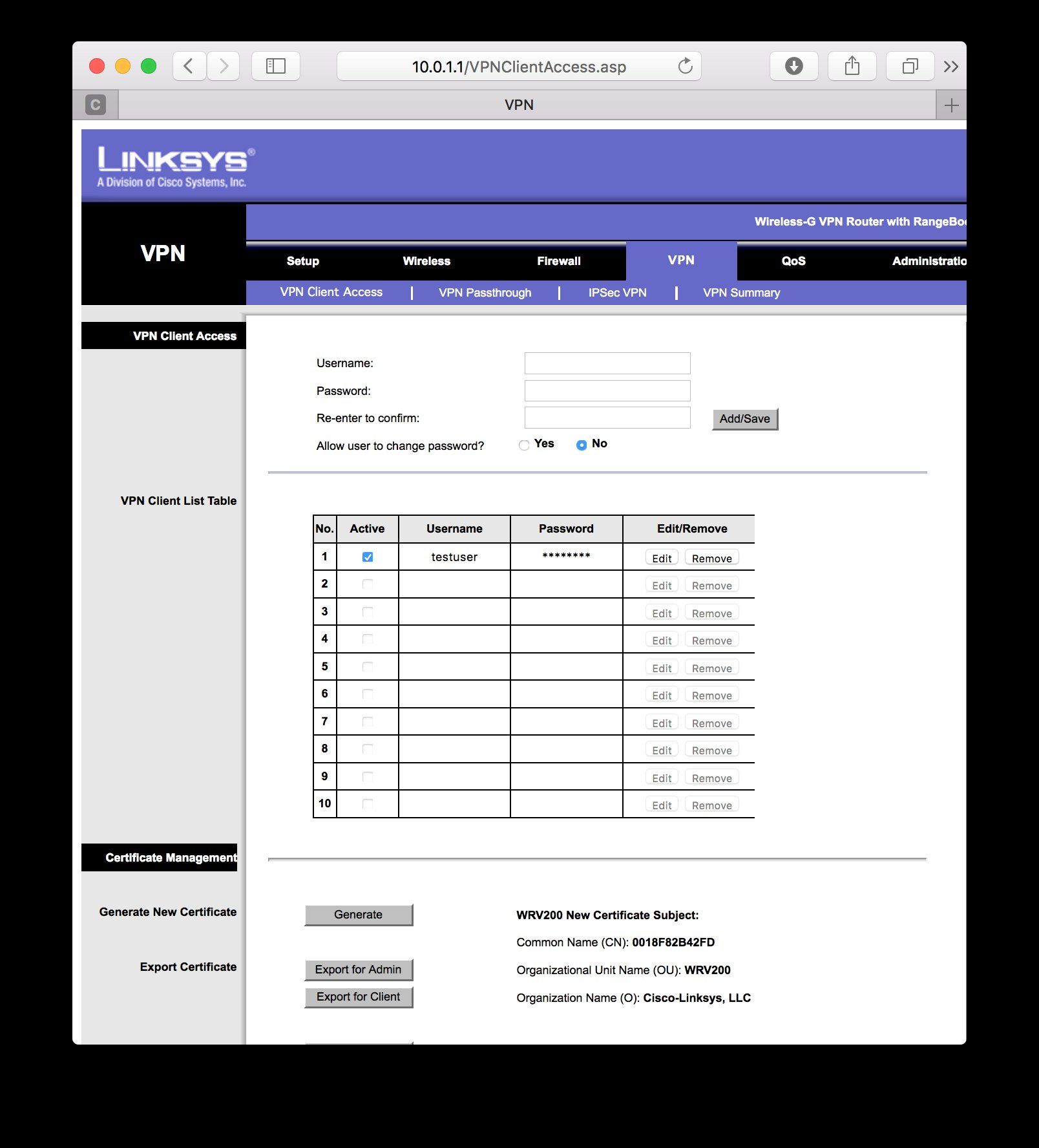
VPN-Beutzer:
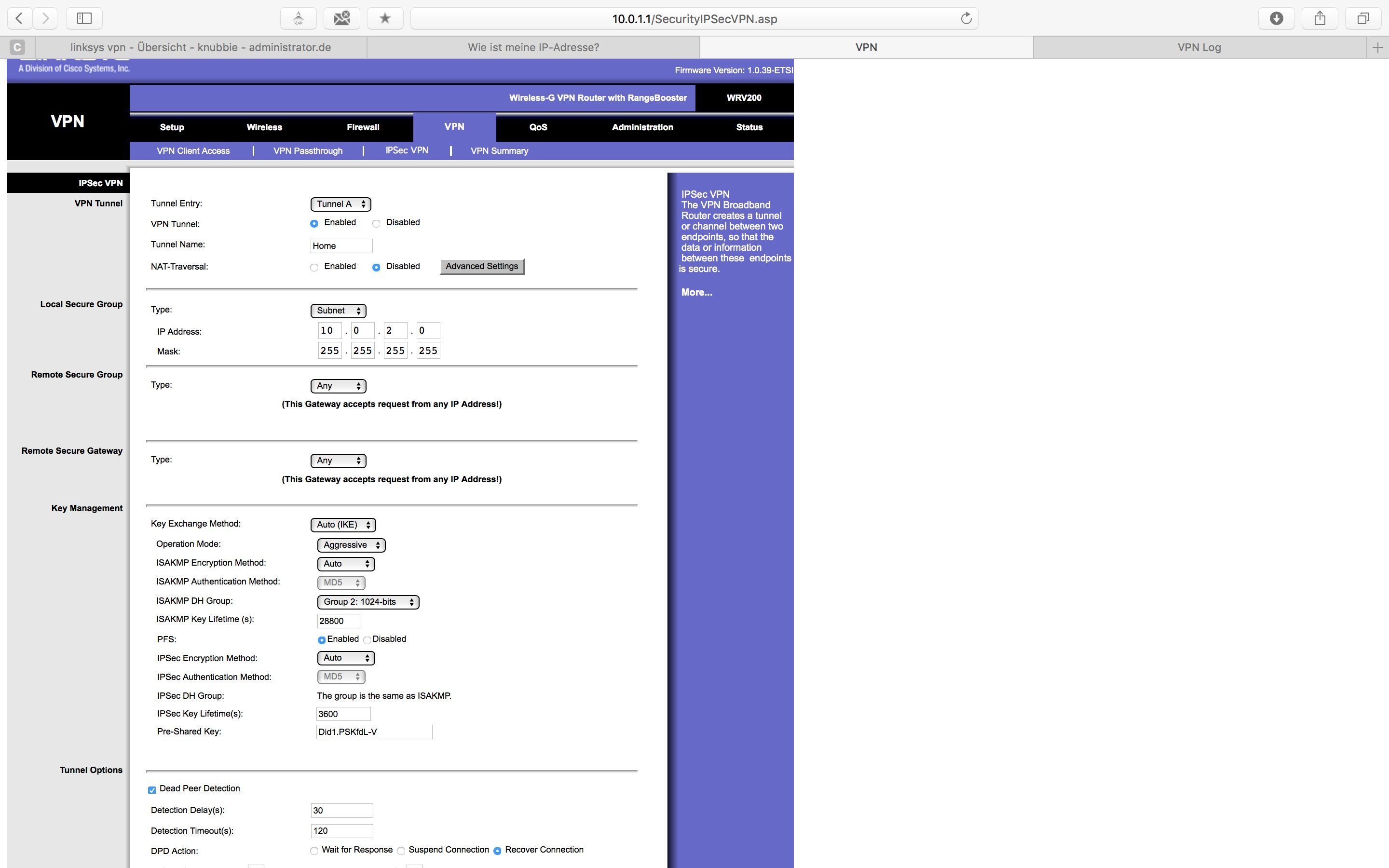
IPSec Einstellungen:
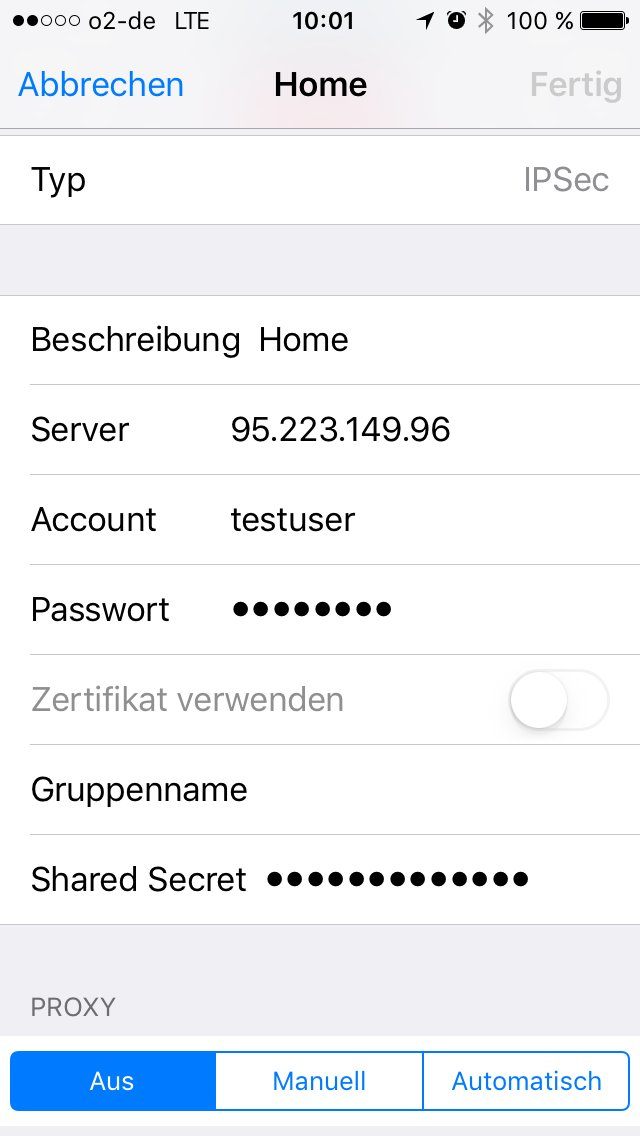
VPN-Client auf dem Phone 6S:
Beim Versuch die VPN-Verbindung mit dem iPhone aufzubauen, erscheint die Meldung:
"Der VPN-Server antwortet nicht"
Das Log vom Linksys sieht so aus:
Ich kenne mich leider zu wenig aus, um das Log interpretieren zu können. Hab mir schon die Finger wund gegoogelt.
Am Log kann man wohl gut erkennen, dass das Problem irgendwie mit der Authentifizierung zu tun haben muss (wenn man sich denn auskennt).
Gibts hier einen Fachmann, der das deuten kann und weiß was zu tun ist?
ich habe ein Netzwerk mit einem Linksys WRV200 Router. Der Router hat die aktuelle Firmware Version. Provider ist Unitymedia mit öffentlicher dynamischer IPv4 IP.
Einziges Gerät im Netz ist ein Macbook (über WLAN).
Internet funktioniert einwandfrei, aber den VPN-IPSec-Servers vom Router bekomme ich nicht ans Laufen.
Folgende Einstellungen habe ich am Router vorgenommen:
WAN und DHCP:
VPN-Beutzer:
IPSec Einstellungen:
VPN-Client auf dem Phone 6S:
Beim Versuch die VPN-Verbindung mit dem iPhone aufzubauen, erscheint die Meldung:
"Der VPN-Server antwortet nicht"
Das Log vom Linksys sieht so aus:
000 [Fri 12:00:25] "TunnelA"[9] 89.204.155.175 #9: responding to Main Mode from unknown peer 89.204.155.175
001 [Fri 12:00:25] "TunnelA"[9] 89.204.155.175 #9: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
002 [Fri 12:00:25] "TunnelA"[9] 89.204.155.175 #9: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
003 [Fri 12:00:25] "TunnelA"[9] 89.204.155.175 #9: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
004 [Fri 12:00:25] "TunnelA"[9] 89.204.155.175 #9: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
005 [Fri 12:00:25] "TunnelA"[9] 89.204.155.175 #9: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
006 [Fri 12:00:25] "TunnelA"[9] 89.204.155.175 #9: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
007 [Fri 12:00:25] "TunnelA"[9] 89.204.155.175 #9: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
008 [Fri 12:00:25] "TunnelA"[9] 89.204.155.175 #9: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
009 [Fri 12:00:25] "TunnelA"[9] 89.204.155.175 #9: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
010 [Fri 12:00:25] "TunnelA"[9] 89.204.155.175 #9: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
011 [Fri 12:00:25] "TunnelA"[9] 89.204.155.175 #9: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
012 [Fri 12:00:25] "TunnelA"[9] 89.204.155.175 #9: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
013 [Fri 12:00:25] "TunnelA"[9] 89.204.155.175 #9: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
014 [Fri 12:00:25] "TunnelA"[9] 89.204.155.175 #9: OAKLEY_DES_CBC is not supported. Attribute OAKLEY_ENCRYPTION_ALGORITHM
015 [Fri 12:00:25] "TunnelA"[9] 89.204.155.175 #9: OAKLEY_DES_CBC is not supported. Attribute OAKLEY_ENCRYPTION_ALGORITHM
016 [Fri 12:00:25] "TunnelA"[9] 89.204.155.175 #9: no acceptable Oakley Transform
017 [Fri 12:00:25] "TunnelA"[9] 89.204.155.175 #9: sending notification NO_PROPOSAL_CHOSEN to 89.204.155.175:41267
018 [Fri 12:00:25] "TunnelA"[9] 89.204.155.175: deleting connection "TunnelA" instance with peer 89.204.155.175 {isakmp=#0/ipsec=#0}
019 [Fri 12:00:28] "TunnelA"[10] 89.204.155.175 #10: responding to Main Mode from unknown peer 89.204.155.175
020 [Fri 12:00:28] "TunnelA"[10] 89.204.155.175 #10: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
021 [Fri 12:00:28] "TunnelA"[10] 89.204.155.175 #10: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
022 [Fri 12:00:28] "TunnelA"[10] 89.204.155.175 #10: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
023 [Fri 12:00:28] "TunnelA"[10] 89.204.155.175 #10: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
024 [Fri 12:00:28] "TunnelA"[10] 89.204.155.175 #10: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
025 [Fri 12:00:28] "TunnelA"[10] 89.204.155.175 #10: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
026 [Fri 12:00:28] "TunnelA"[10] 89.204.155.175 #10: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
027 [Fri 12:00:28] "TunnelA"[10] 89.204.155.175 #10: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
028 [Fri 12:00:28] "TunnelA"[10] 89.204.155.175 #10: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
029 [Fri 12:00:28] "TunnelA"[10] 89.204.155.175 #10: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
030 [Fri 12:00:28] "TunnelA"[10] 89.204.155.175 #10: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
031 [Fri 12:00:28] "TunnelA"[10] 89.204.155.175 #10: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
032 [Fri 12:00:28] "TunnelA"[10] 89.204.155.175 #10: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
033 [Fri 12:00:29] "TunnelA"[10] 89.204.155.175 #10: OAKLEY_DES_CBC is not supported. Attribute OAKLEY_ENCRYPTION_ALGORITHM
034 [Fri 12:00:29] "TunnelA"[10] 89.204.155.175 #10: OAKLEY_DES_CBC is not supported. Attribute OAKLEY_ENCRYPTION_ALGORITHM
035 [Fri 12:00:29] "TunnelA"[10] 89.204.155.175 #10: no acceptable Oakley Transform
036 [Fri 12:00:29] "TunnelA"[10] 89.204.155.175 #10: sending notification NO_PROPOSAL_CHOSEN to 89.204.155.175:41267
037 [Fri 12:00:29] "TunnelA"[10] 89.204.155.175: deleting connection "TunnelA" instance with peer 89.204.155.175 {isakmp=#0/ipsec=#0}
038 [Fri 12:00:32] "TunnelA"[11] 89.204.155.175 #11: responding to Main Mode from unknown peer 89.204.155.175
039 [Fri 12:00:32] "TunnelA"[11] 89.204.155.175 #11: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
040 [Fri 12:00:32] "TunnelA"[11] 89.204.155.175 #11: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
041 [Fri 12:00:32] "TunnelA"[11] 89.204.155.175 #11: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
042 [Fri 12:00:32] "TunnelA"[11] 89.204.155.175 #11: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
043 [Fri 12:00:32] "TunnelA"[11] 89.204.155.175 #11: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
044 [Fri 12:00:32] "TunnelA"[11] 89.204.155.175 #11: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
045 [Fri 12:00:32] "TunnelA"[11] 89.204.155.175 #11: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
046 [Fri 12:00:32] "TunnelA"[11] 89.204.155.175 #11: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
047 [Fri 12:00:32] "TunnelA"[11] 89.204.155.175 #11: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
048 [Fri 12:00:32] "TunnelA"[11] 89.204.155.175 #11: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
049 [Fri 12:00:32] "TunnelA"[11] 89.204.155.175 #11: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
050 [Fri 12:00:32] "TunnelA"[11] 89.204.155.175 #11: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
051 [Fri 12:00:32] "TunnelA"[11] 89.204.155.175 #11: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
052 [Fri 12:00:32] "TunnelA"[11] 89.204.155.175 #11: OAKLEY_DES_CBC is not supported. Attribute OAKLEY_ENCRYPTION_ALGORITHM
053 [Fri 12:00:32] "TunnelA"[11] 89.204.155.175 #11: OAKLEY_DES_CBC is not supported. Attribute OAKLEY_ENCRYPTION_ALGORITHM
054 [Fri 12:00:32] "TunnelA"[11] 89.204.155.175 #11: no acceptable Oakley Transform
055 [Fri 12:00:32] "TunnelA"[11] 89.204.155.175 #11: sending notification NO_PROPOSAL_CHOSEN to 89.204.155.175:41267
056 [Fri 12:00:32] "TunnelA"[11] 89.204.155.175: deleting connection "TunnelA" instance with peer 89.204.155.175 {isakmp=#0/ipsec=#0}
057 [Fri 12:00:35] "TunnelA"[12] 89.204.155.175 #12: responding to Main Mode from unknown peer 89.204.155.175
058 [Fri 12:00:35] "TunnelA"[12] 89.204.155.175 #12: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
059 [Fri 12:00:35] "TunnelA"[12] 89.204.155.175 #12: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
060 [Fri 12:00:35] "TunnelA"[12] 89.204.155.175 #12: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
061 [Fri 12:00:35] "TunnelA"[12] 89.204.155.175 #12: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
062 [Fri 12:00:35] "TunnelA"[12] 89.204.155.175 #12: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
063 [Fri 12:00:35] "TunnelA"[12] 89.204.155.175 #12: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
064 [Fri 12:00:35] "TunnelA"[12] 89.204.155.175 #12: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
065 [Fri 12:00:35] "TunnelA"[12] 89.204.155.175 #12: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
066 [Fri 12:00:35] "TunnelA"[12] 89.204.155.175 #12: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
067 [Fri 12:00:35] "TunnelA"[12] 89.204.155.175 #12: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
068 [Fri 12:00:35] "TunnelA"[12] 89.204.155.175 #12: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
069 [Fri 12:00:35] "TunnelA"[12] 89.204.155.175 #12: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
070 [Fri 12:00:35] "TunnelA"[12] 89.204.155.175 #12: policy does not allow Extended Authentication (XAUTH) of initiator (we are responder). Attribute OAKLEY_AUTHENTICATION_METHOD
071 [Fri 12:00:35] "TunnelA"[12] 89.204.155.175 #12: OAKLEY_DES_CBC is not supported. Attribute OAKLEY_ENCRYPTION_ALGORITHM
072 [Fri 12:00:35] "TunnelA"[12] 89.204.155.175 #12: OAKLEY_DES_CBC is not supported. Attribute OAKLEY_ENCRYPTION_ALGORITHM
073 [Fri 12:00:35] "TunnelA"[12] 89.204.155.175 #12: no acceptable Oakley Transform
074 [Fri 12:00:35] "TunnelA"[12] 89.204.155.175 #12: sending notification NO_PROPOSAL_CHOSEN to 89.204.155.175:41267
075 [Fri 12:00:35] "TunnelA"[12] 89.204.155.175: deleting connection "TunnelA" instance with peer 89.204.155.175 {isakmp=#0/ipsec=#0} Ich kenne mich leider zu wenig aus, um das Log interpretieren zu können. Hab mir schon die Finger wund gegoogelt.
Am Log kann man wohl gut erkennen, dass das Problem irgendwie mit der Authentifizierung zu tun haben muss (wenn man sich denn auskennt).
Gibts hier einen Fachmann, der das deuten kann und weiß was zu tun ist?
Please also mark the comments that contributed to the solution of the article
Content-Key: 332475
Url: https://administrator.de/contentid/332475
Printed on: April 25, 2024 at 11:04 o'clock
5 Comments
Latest comment
Deine IPsec Einstellungen sind wieder falsch !!
Die Fehlermeldungen lassen allerdings vermuten das der Router nur 3DES kann und die neuen von Apple vorgeschriebenen Schlüsselalgorythmen nicht supportet weil er doch schon zu alt ist und sehr lange keine FW Aktualisierung mehr bekommen hat. Der WRV200 ist End of Life
Poste mal die Log Meldungen mit den angepassten Settings.
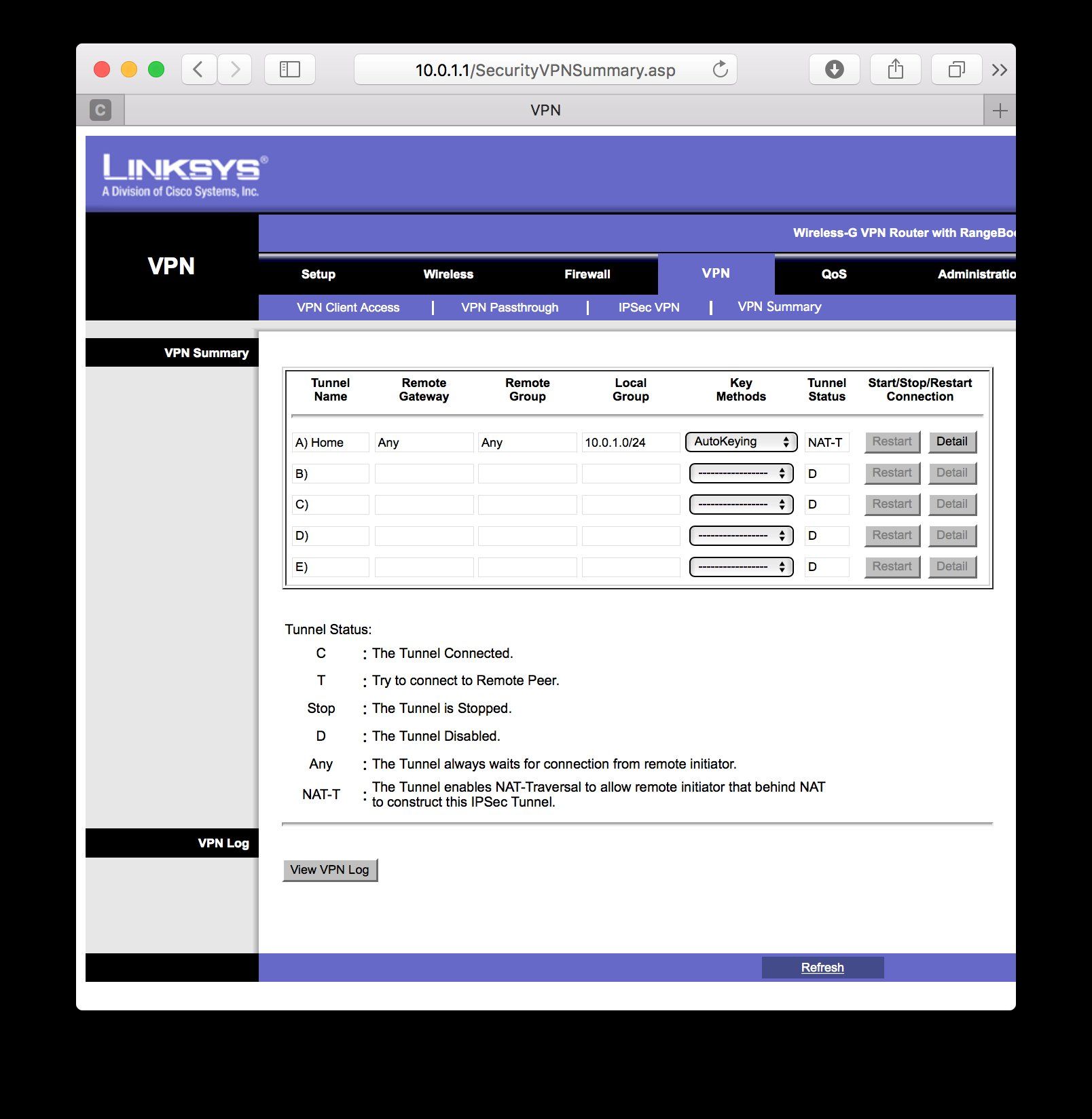
Was ist mit den Einstellungen unter "VPN Client Access" und "VPN Summary" ??? Hier fehlen die Screenshots. Gerade der Client Access mit der Group Einstellung ist wichtig !
Alternativ kannst du den Zugriff mal mit dem MacBook testen ob der native IKE2 Client dort die verbindung aufbauen kann.
Internet Dokus sind sehr spärlich
http://www.lobotomo.com/products/IPSecuritas/howto/Linksys%20WRV200%20H ...
Ggf. hilft vielleicht noch die FritzBox Doku:
https://avm.de/service/vpn/tipps-tricks/vpn-verbindung-zur-fritzbox-unte ...
- NAT Traversal MUSS zwingend auf enabled ! Du musst ja die NAT Firewall des Routers überwinden !
- Type Subnet ist falsch ! Hier muss dein lokales Subnet rein und das lautet ja nun mal 10.0.1.0 255.255.255.0 !!
- Statt MD5 Authentication kannst du besser SHA nehmen aber vermutlich macht er das automatisch, da es ausgegraut ist und die Methode auf "Auto" steht.
Die Fehlermeldungen lassen allerdings vermuten das der Router nur 3DES kann und die neuen von Apple vorgeschriebenen Schlüsselalgorythmen nicht supportet weil er doch schon zu alt ist und sehr lange keine FW Aktualisierung mehr bekommen hat. Der WRV200 ist End of Life
Poste mal die Log Meldungen mit den angepassten Settings.
Was ist mit den Einstellungen unter "VPN Client Access" und "VPN Summary" ??? Hier fehlen die Screenshots. Gerade der Client Access mit der Group Einstellung ist wichtig !
Alternativ kannst du den Zugriff mal mit dem MacBook testen ob der native IKE2 Client dort die verbindung aufbauen kann.
Internet Dokus sind sehr spärlich
http://www.lobotomo.com/products/IPSecuritas/howto/Linksys%20WRV200%20H ...
Ggf. hilft vielleicht noch die FritzBox Doku:
https://avm.de/service/vpn/tipps-tricks/vpn-verbindung-zur-fritzbox-unte ...
Wenn ich dort statt Auto eines der 3 anderen auswähle,
Wieso 3...ich zähle 4 Apple schreibt m.W. AES 256 vor. Also wenn du das aus Auto lässt sollte das OK sein dann kaspern die Beteiligten das dynamisch aus.
Die Fehlermeldungen im Log sagen aber aus das der WRT200 kein XAUTH supportet. Damit wirst du dann mit aktuellen IPsec Clients nix mehr
Wenn du mal nach der Fehlermeldung suchst "policy does not allow Extended Authentication xauth" dann findet man viele Einträge dazu.
Vermutlich bist du mit einer kleinen aktuellen Firewall oder einer FritzBox besser bedient:
Preiswerte, VPN fähige Firewall im Eigenbau oder als Fertiggerät
Die kann das alles problemlos umsetzen:
IPsec VPN Praxis mit Standort Vernetzung Cisco, Mikrotik, pfSense, FritzBox u.a